Hello All!
Ive been inspired to write this after seeing a thread on Reddit where, or so the story goes, a son had estranged himself from his father and left the household but the father had the family PCs enrolled into an Autopilot / MEM instance and wiped the sons PC. When the son tried to reboot into the PC he was met with the branded Autopilot screen and not wanting to be under his fathers control reached out to Reddit to see how he could avoid Autopilot and re-enrollment.
This got me curious as to all the ways that could be accomplished. Conversely you could follow the opposite of this post to enforce Autopilot in your organization.
It used to be very easy, but MS has patched quite a few of the holes. In 1903 they removed the ability to start the process but hit the go back button to get to the unbranded sign in screen which would allow a local user account.
At some point they added in the control in the Autopilot profile to hide the change account options.
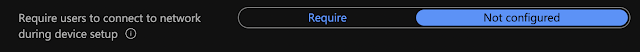
At some point they also introduced a setting that requires internet connectivity during OOBE to proceed. This CSP flips whats called a UEFI variable and persists through a machine wipe. This means that during first time setup this would not be set, since it's not enrolled at that time, but subsequent wipes would be protected.
With that background info in mind lets get back to our Reddit user. For this initial workaround let's just assume that neither control is deployed. Its default state is not configured so it's not too far of a stretch.
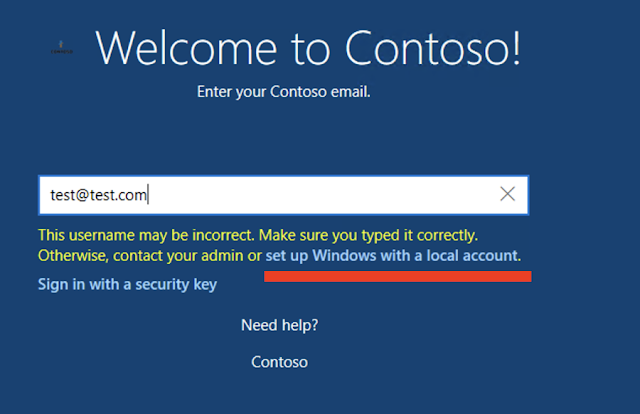
With the account change options set to 'show' all the end user would have to do would be to choose to "domain join" instead or enter an improper email address / password enough times and they would be presented with the option to create a local user instead, like below.
Ideally, now with no Autopilot.json file and with a shiny new local admin account thats past the OOBE the machine should be free from management, for now anyways, until the next device reset.
As for the additional setting or require network during OOBE that stamps the UEFI variables...we are going to have to wait on that. I do not currently know how to change those but when I figure it out I will update this post. My initial thought is that you can launch powershell and change them in some manner in that way or possibly even from the built in preboot UEFI interface.
For now, remove the .json and don't connect to the internet when you are going through the OOBE....or ya know, just re-image with Windows Home as that doesn't even check into the Autopilot service!
Until next time!